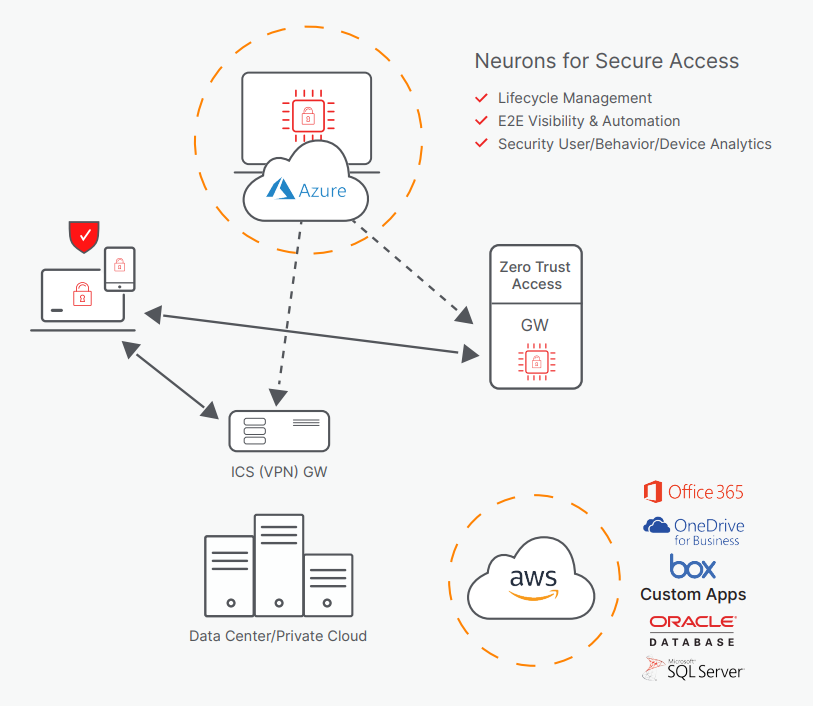
Guide to Securing Remote Access Software Industrial Cyber(05)

This image is part of a curated gallery related to Ultimate Guide To Secure Hapo Login Access. All visuals are selected to provide relevant visual reference for the topic.
Image gallery: Ultimate Guide To Secure Hapo Login Access